«LEAK» Iam Hely 2026 Storage All Files Download
Looking for the latest iam hely exclusive feed updated for 2026. We offer the most complete database of premium video content and full image galleries. Unlike other sites, we offer one-click media downloads without any hidden costs. Enjoy iam hely with crystal-clear photo quality. The current media pack features exclusive PPV videos, behind-the-scenes photos, and rare digital files. Stay updated with the newest iam hely photo additions. Access the full folder today to save the files to your device.
Learn about identity and access management (iam) and how it helps organizations secure, manage, and define roles and access privileges for users and identities. Iam solutions ensure the right individuals have access to the right it resources, for the right reasons, at the right time. The iam is the international professional body for whole life management of physical assets
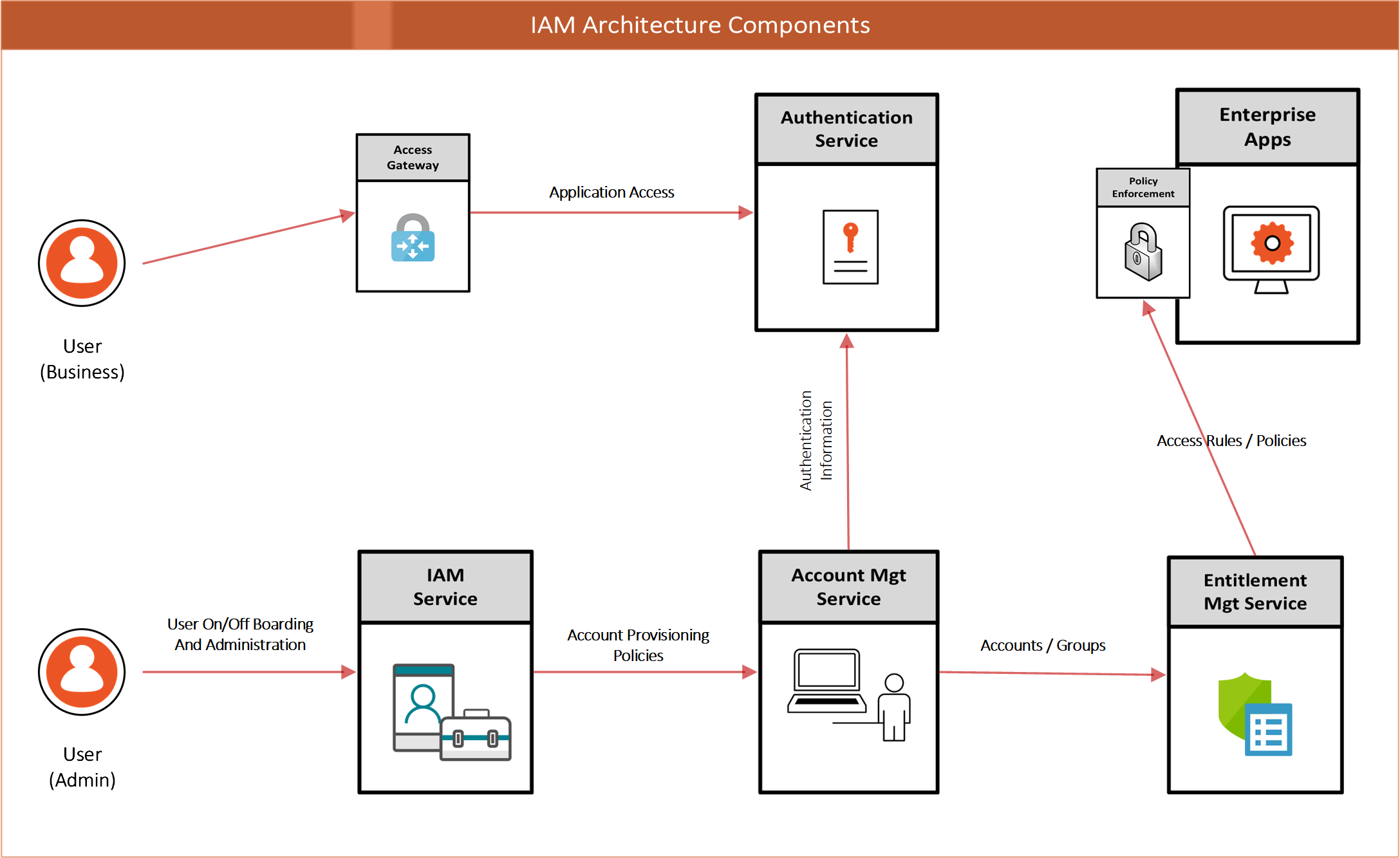
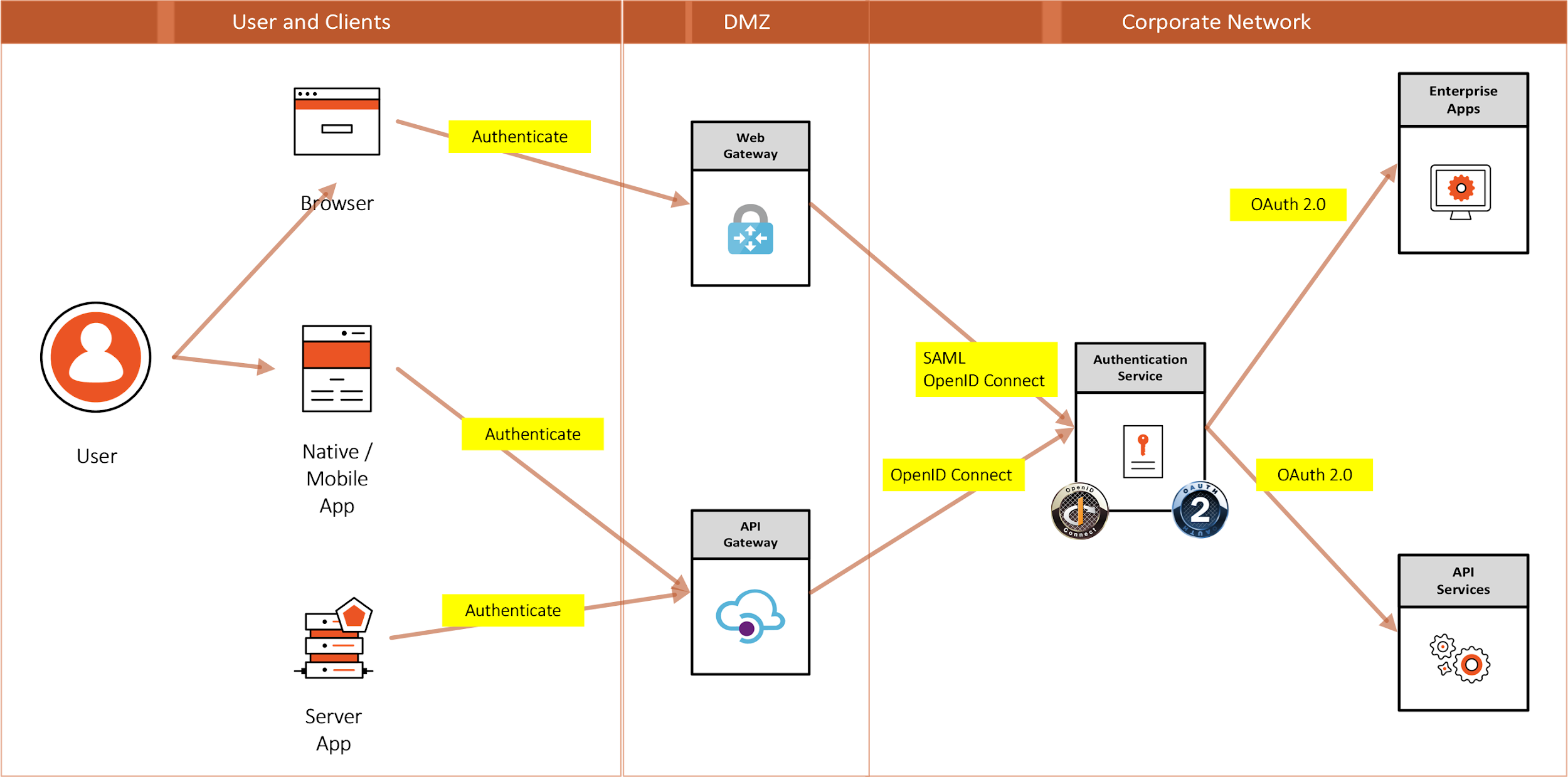
Cameron | Introduction to IAM Architecture (v2) | IDPro Body of Knowledge
Learn about aws identity and access management (iam), its features, and basic concepts. It and security organizations use identity and access management (iam) solutions to administer user identities and control access to enterprise resources Identity management, otherwise known as identity and access management (iam) is an identity security framework that works to authenticate and authorize user access to resources such as applications, data, systems, and cloud platforms.
Learn the core concepts of identity and access management (iam), including authentication, authorization, and identity providers, to secure resources effectively.
Identity and access management (iam) is a framework of policies, processes, and technologies that enable organizations to manage digital identities and control user access to critical corporate information. Identity and access management (iam) is the cybersecurity discipline that deals with provisioning and protecting digital identities and user access permissions in an it system Iam tools help ensure that the right people can access the right resources for the right reasons at the right time. Identity and access management (iam) is a framework that allows the it team to control access to systems, networks and assets based on each user’s identity.