〚NEW〛 Sextortion Email Scam 2024 2026 Storage Videos & Photos Download
Unlock the full sextortion email scam 2024 premium vault freshly updated today. We offer the most complete database of premium video content and full image galleries. Unlike other sites, we offer instant file access completely free for our community. Enjoy sextortion email scam 2024 in stunning 4K clarity. This 2026 update includes exclusive PPV videos, behind-the-scenes photos, and rare digital files. Stay updated with the newest sextortion email scam 2024 photo additions. Start your fast download immediately to unlock the premium gallery.
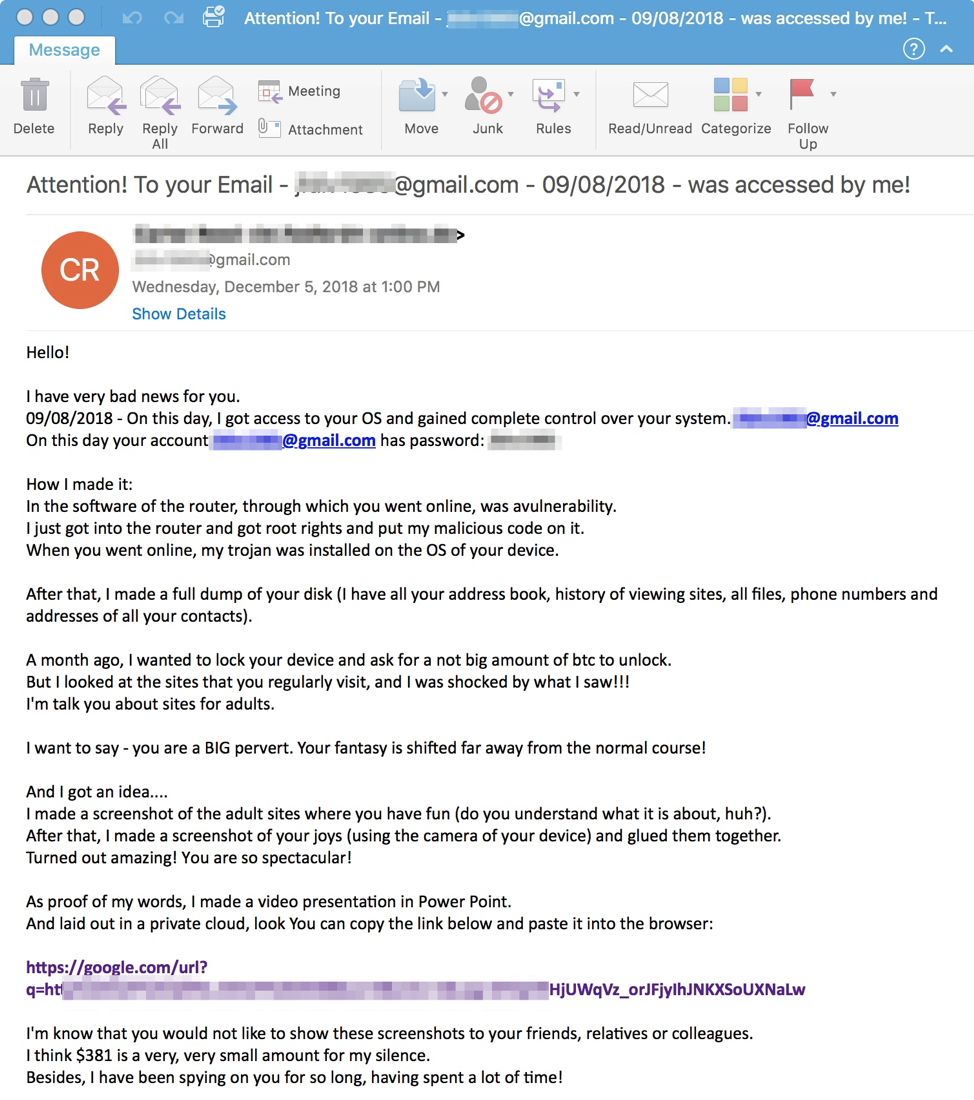
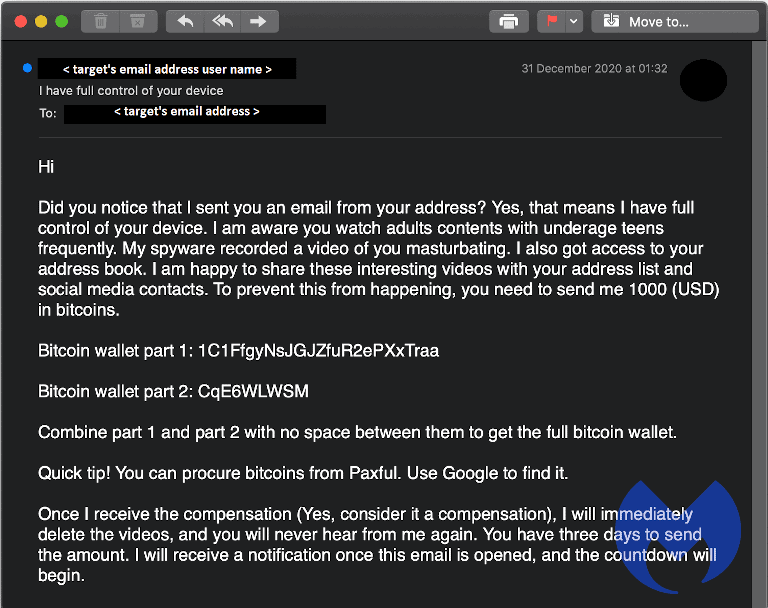
An old but persistent email scam known as “sextortion” has a new personalized touch Unlike traditional scams that rely on generic phishing tactics, this new variant uses personal images and information to create a sense of fear and urgency. The missives, which claim that malware has captured webcam footage of recipients pleasuring themselves, now.
What is Sextortion malware scam? and how to protect yourself from it
Getting emails from someone trying to blackmail you for money In 2024, a particularly alarming scam emerged Bbb warns consumers about sextortion emails.
hello pervert sextortion mails keep adding new features to their email to increase credibility and urge victims to pay
Another variety of sextortion is a scam email accusing the recipient of possessing child pornography The sender claims to be work for law enforcement and is preparing a list of pedophiles for mass arrest The recipient is among them, states the email To get their name removed from the list, the victim is invited to pay a ransom.
The hacker promises to go away if you send them thousands of dollars, usually with bitcoin This is different from a separate sextortion scam in which a stranger befriends and convinces a user to exchange sexual content then demands payment for secrecy A much more perilous situation which requires a more careful response. Feb 3, 2025 email scams have been a persistent threat to individuals and businesses for years, constantly evolving to exploit new vulnerabilities and technologies