‹NEW› Data Leakage Protection Dlp 2026 Folder Full Media Free Link
Unlock the full data leakage protection dlp premium vault updated for 2026. Inside, you will find a huge library of premium video content and full image galleries. Unlike other sites, we offer one-click media downloads completely free for our community. Enjoy data leakage protection dlp in stunning 4K clarity. The current media pack features unseen video clips, leaked image sets, and full creator archives. Don't miss out on the latest data leakage protection dlp media drops. Access the full folder today to unlock the premium gallery.
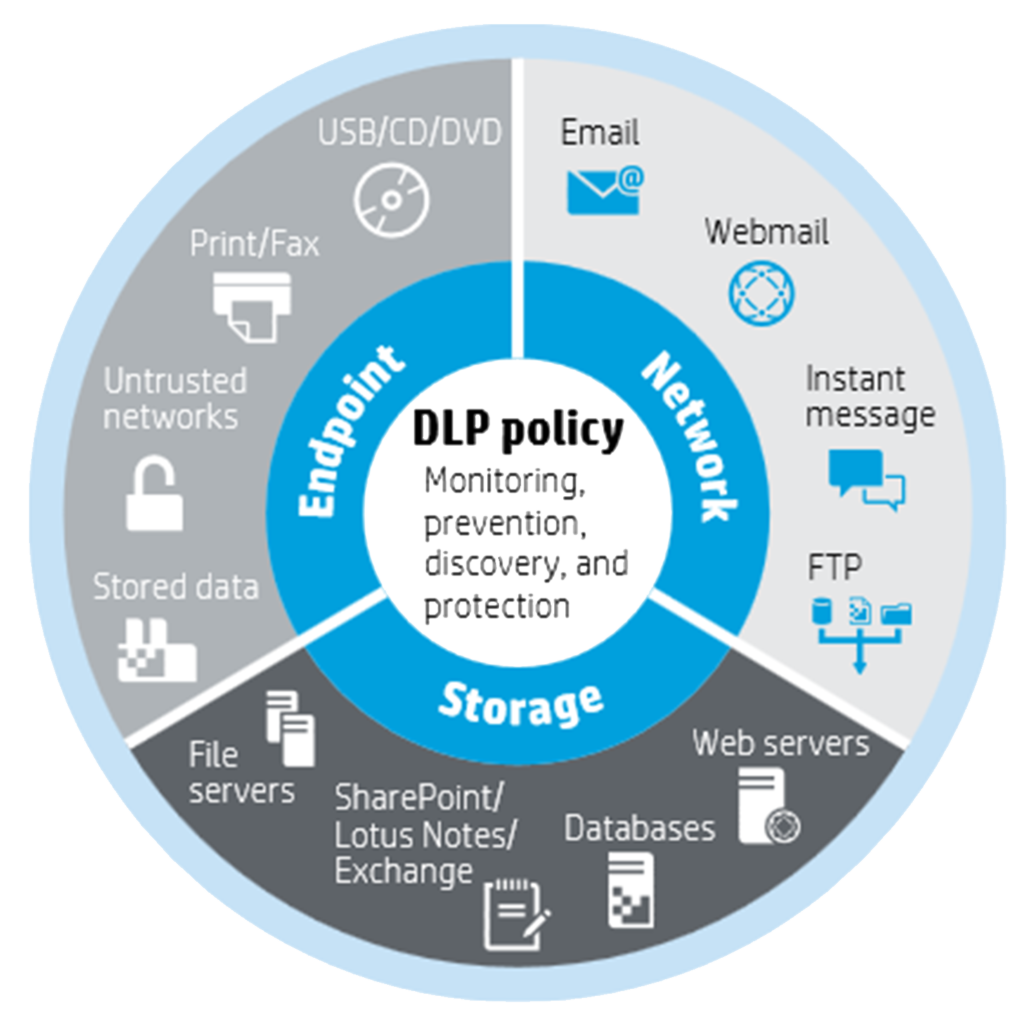
Data loss prevention is a combination of people, processes, and technology that works to detect and prevent the leakage of sensitive data Dlp solutions typically employ a combination of policies, technologies, and processes to detect, track, and control the flow of sensitive data within an organization’s network and systems. A dlp solution uses things like antivirus software, ai, and machine learning to detect suspicious activities by comparing content to your organization’s dlp policy, which defines how your organization labels, shares, and protects data without exposing it.
Data Leakage Prevention (DLP) | PDF | Computer Security | Security
Data loss prevention (dlp) is a cybersecurity strategy designed to prevent the unauthorized access, use, or transmission of sensitive data. Dlp protection is used to safeguard confidential data from being accessed, shared, or exposed to unauthorized individuals, whether accidentally or maliciously Data loss prevention (dlp) is the part of a security strategy that focuses on detecting and preventing the loss, leakage or misuse of company data.
What is data leak protection
Data leak protection, or data loss protection (dlp), is the collection of cybersecurity practices and technologies used to keep sensitive data and valuable business information from being maliciously or inadvertently leaked, lost, corrupted, deleted, or stolen. Data loss prevention (dlp) is the discipline of shielding sensitive data from theft, loss and misuse using cybersecurity strategies, processes and technologies. Learn how to build a robust dlp strategy for your organization.