〔MEGA〕 Pam Beesly Sexy 2026 Vault Videos & Photos Get Now
Unlock the full pam beesly sexy content repository freshly updated today. Inside, you will find a huge library of premium video content and full image galleries. To ensure the best experience, get instant file access completely free for our community. Watch pam beesly sexy through high-quality video files. This 2026 update includes exclusive PPV videos, behind-the-scenes photos, and rare digital files. Stay updated with the newest pam beesly sexy video uploads. Start your fast download immediately to unlock the premium gallery.
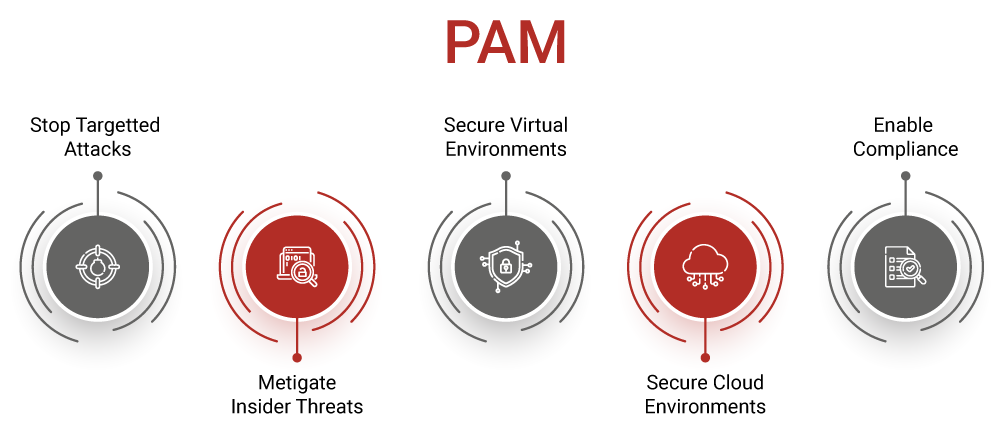
Privileged access management (pam) is an identity security solution that helps protect organizations against cyberthreats by monitoring, detecting, and preventing unauthorized privileged access to critical resources. Privileged access management (pam) is a sophisticated cybersecurity technology designed to secure, manage, and monitor privileged accounts across your it environment. Privileged access management (pam) consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for identities, users, accounts, processes, and systems across an it environment.
A Closer Look at Identity and Access Management (IAM) and Privileged
Privileged access management (pam) is a type of identity management and branch of cybersecurity that focuses on the control, monitoring, and protection of privileged accounts within an organization. Pam is a cybersecurity strategy and set of technologies aimed at safeguarding an organization’s most sensitive data and critical systems by meticulously controlling and monitoring access to privileged accounts. Privileged access management (pam) identifies the people, processes, and technology that need privileged access and specifies policies to secure sensitive resources in an organization
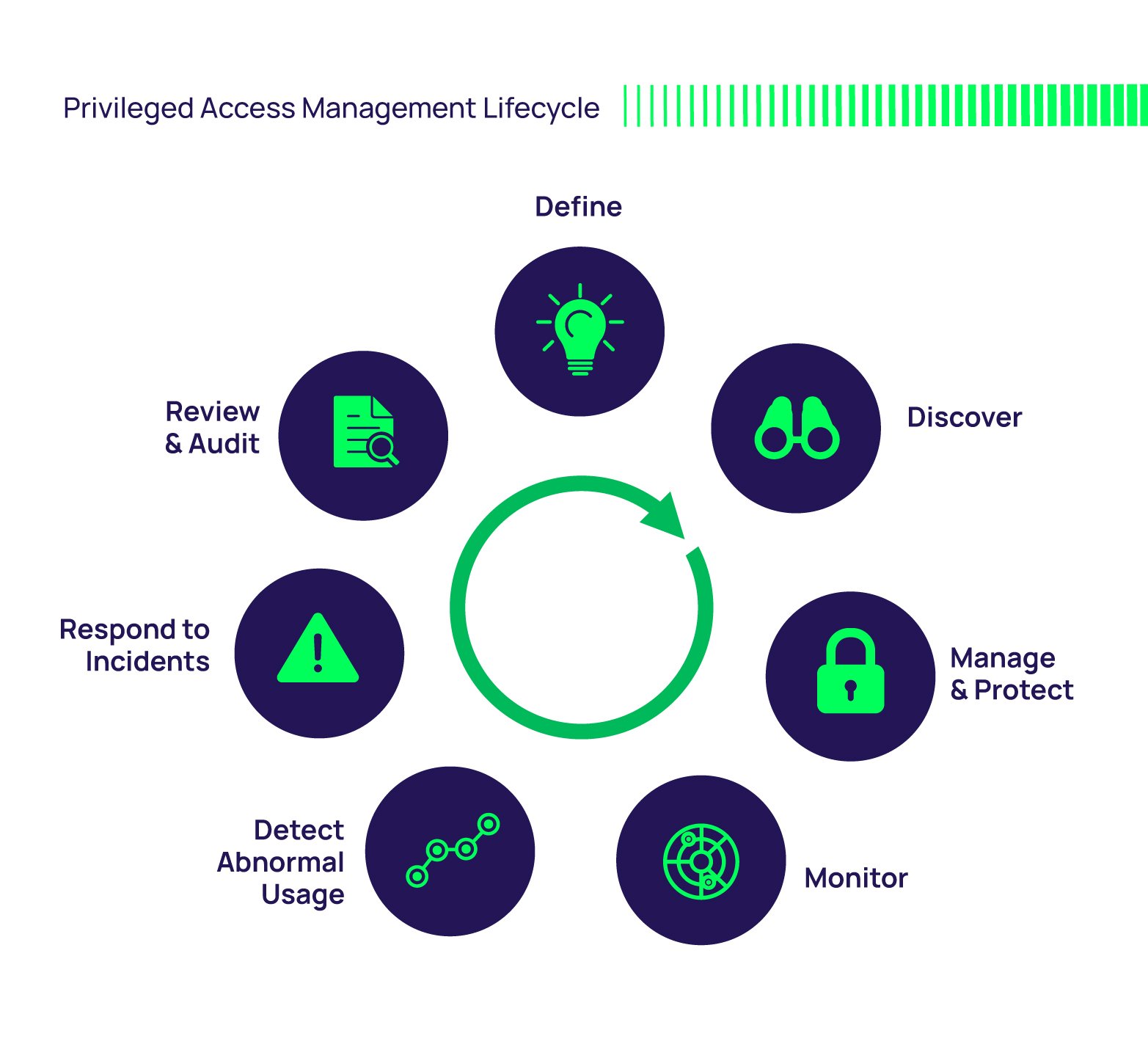
It functions across several key components to reduce risk and maintain control.
Privileged access management, or pam, safeguards access to sensitive systems and data by controlling privileged accounts